KB Article #177856
How do you specify an Ephemeral DH key parameter on an HTTPS port?
Problem
* How do you specify an Ephemeral DH key parameter on an HTTPS port?
Resolution
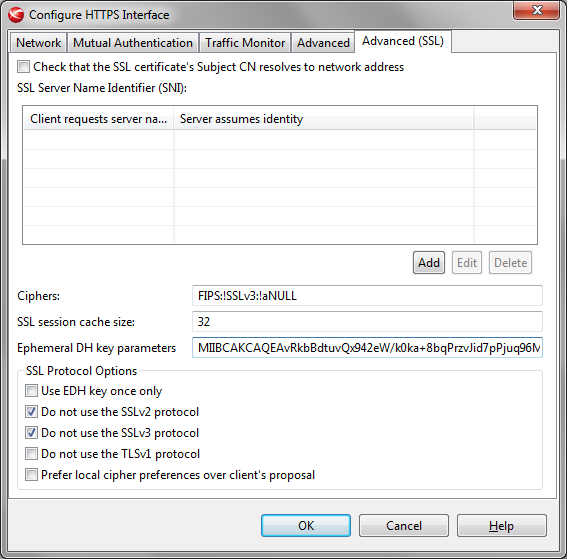
First, be sure to generate your own DH parameter. The Logjam vulnerability is that commonly used DH parameters can be partially broken ahead of time, allowing an adversary to do most of the work required to decrypt your traffic by knowing your DH modulus. Be sure to get guidance from your security people about the recommended size. You can generate a DH parameter via OpenSSL, for example this command will create a 2048 bit parameter:
openssl dhparam -out dhparams.pem 2048
Before placing the parameter in the configuration, you have to remove all line breaks as well as the BEGIN/END block. So you use only a base64 blob containing a single DH parameter, for example:
MIIBCAKCAQEAvRkbBdtuvQx942eW/k