KB Article #183132
How to update the sample certificates for AIS 2.2.1 - 2.4.0
Problem
On the 14th of March 2024, the SSLCert Tomcat server and the SSO agent certificates delivered with AIS infrastructure will expire.
Please refer to KB Article #183062 for instructions on changing the Default Axway Certificates on PassPort side first. If you no longer use PassPort and have replaced it with Portal IAM, please check the procedure #3 below.
Please also note that PassPort will reach its End of Life on Feb 29th 2024 and a support extension will be necessary if you still plan on using it.
Resolution
Although Axway strongly advises against the usage of sample certificates (especially for production purposes) we’re going to present a procedure for changing these certificates for testing purposes.
If you are using your own custom certificates for SSO and SSL then you are not impacted by the expiration of these certificates.
For specific information regarding the usage/replacement of custom certificates please refer to the InterPlay Security Guide (login required), Change the HTTPS server certificate section (Configuration > Security Configuration).
The purpose of this document is to treat the case when the actual Axway sample certificates are to be replaced by newer Axway certificates, with modified expiration date.
Products/versions impacted:
The following products and versions are impacted, regardless if you are using PassPort or Portal IAM as your access manager:
- Interplay 2.2.1 / 2.3.0 / 2.4.0
- AIS Designer 2.2.1 / 2.3.0 / 2.4.0
- AdministrationUI 2.2.1 / 2.3.0 / 2.4.0
- DatastoreClient 2.2.1 / 2.3.0 / 2.4.0
- Report 2.2.1 / 2.3.0 / 2.4.0
- Rule Engine Server 2.2.1 / 2.3.0 / 2.4.0
- AIS Studio 2.4.0
- AIS Portal 2.4.0
The new FAH 3.0 is not impacted as it uses a newer, safer, easier to use generation method for default certificates and does not require applying this manual procedure.
In the case where PassPort is used for authentication by the Axway products, following the KB Article #183062 is mandatory for this procedure.
This procedure must be implemented on each AIS product installation. So if you have separate installations for InterPlay, Datastore, Designer, Report, Rule Server, Portal, etc., you need to upgrade each one separately with the same procedure.
Introduction
In order to decide on what procedure to use (1. Only sample certificates / 2. Sample certificates combined with custom ones), please run the following command before replacing each of the provided keystores.
keytool -v -list -keystore <keystore-file-name>
The password is not mandatory for this command to work.
Examine the output of the command and confirm that no custom certificates are present in that keystore. All of the old sample certificates are issued by root CA [ CN=PassPort, OU=R&D, O=Axway, L=Bucharest, C=RO] that expires on Thu Mar 14 00:59:59 CET 2024.
If you are already using only your own custom certificates then this KB does not apply and you are not impacted by the expiration dates of the sample certificates.
- If you are using only the Axway sample certificates then please implement the actions described at point #1 below.
- Otherwise, if you are using both Axway sample certificates and your own certificates then please implement the actions described at #2.
- If you use the AIS components with Portal IAM instead of PassPort, please proceed to #3.
NOTE: in order to confirm if you're using CAS SSO or not, and therefore decide if you need to change the ssofilter certificates as well (or not), here's what having CAS SSO configured looks like in PassPort and Administration UI:
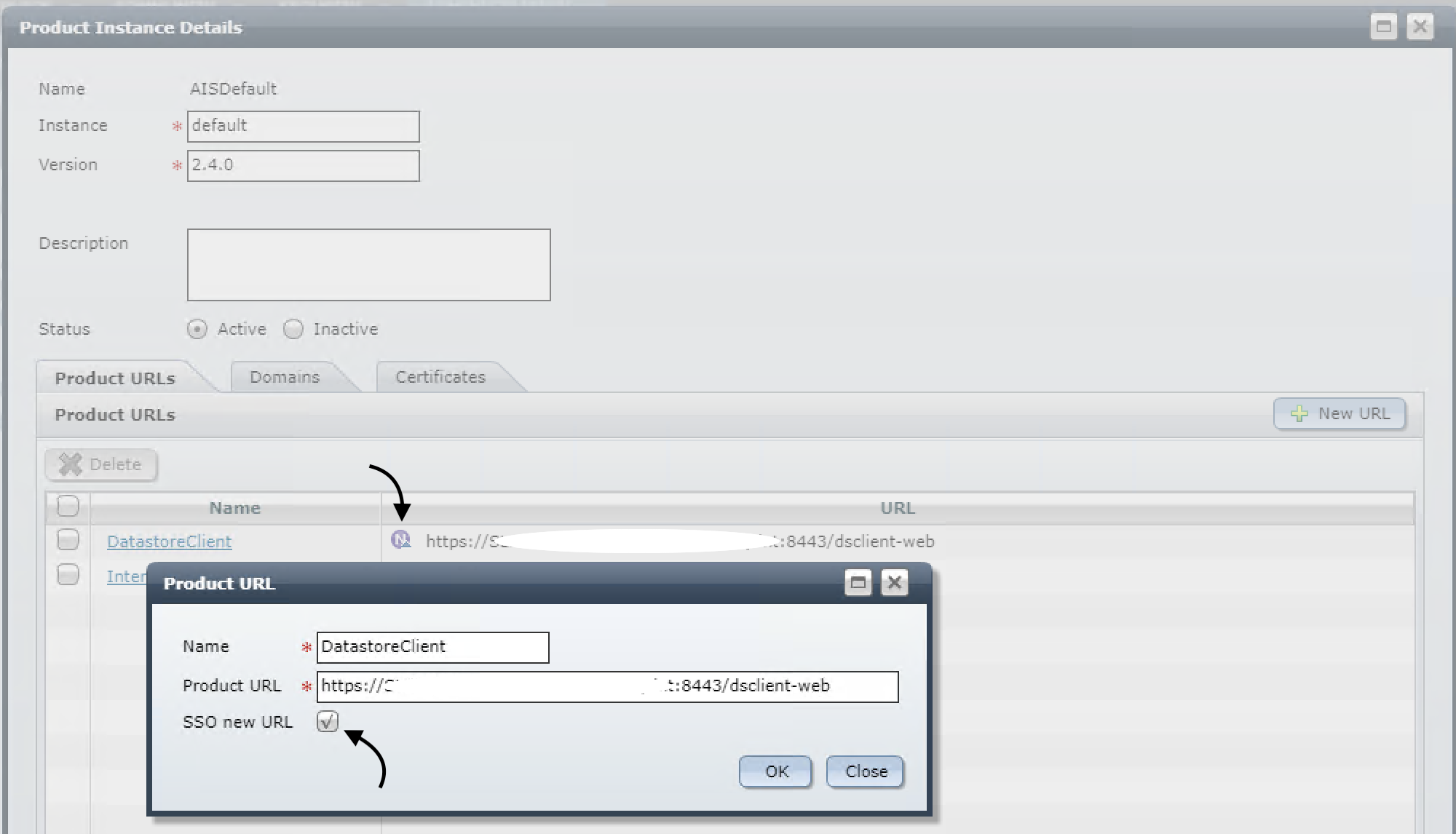
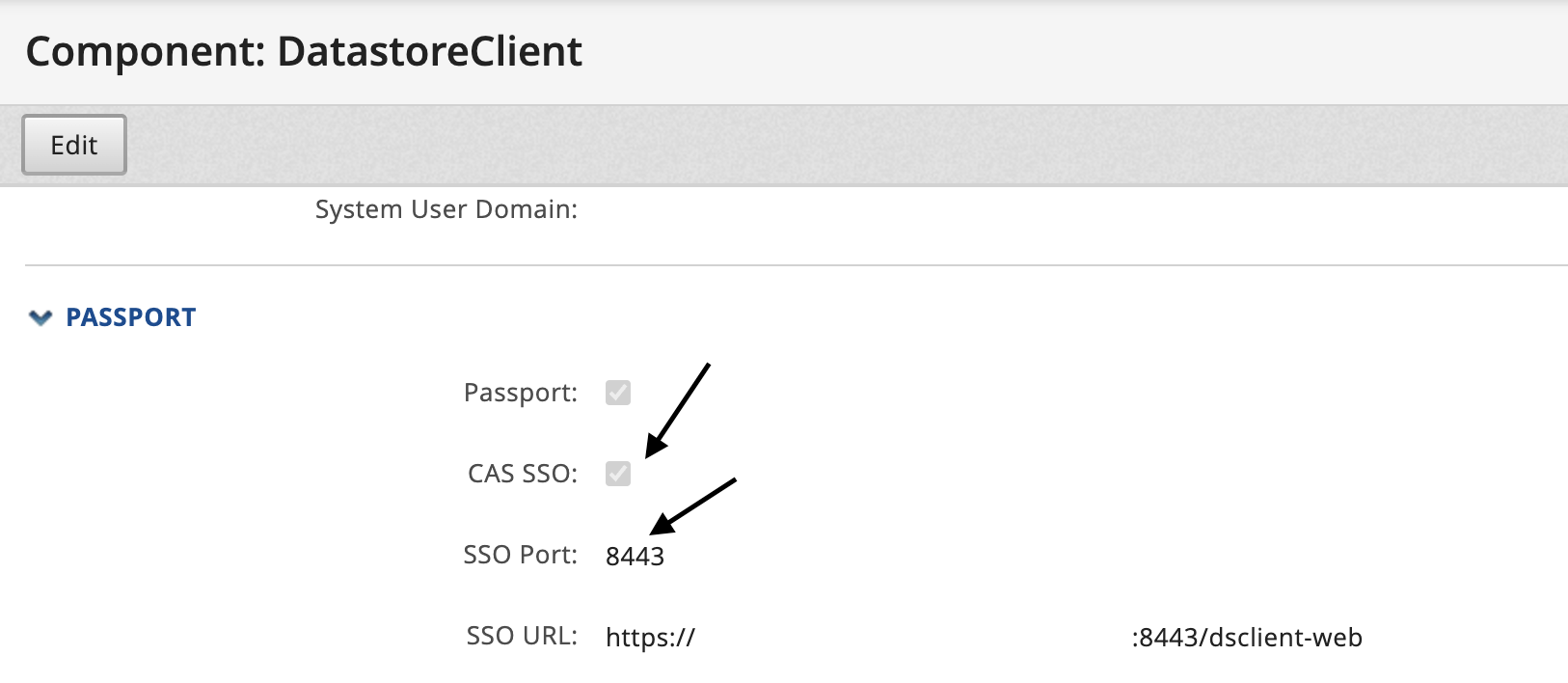
1. Update certificates for installations with PassPort that use only sample certificates
Download the new sample certificates attached to this KB (New_Sample_Certificates_2024.zip)
Certs
- keystore.jks → Tomcat private certificates
- truststorePassPort.jks → trusted certificates used for selfregistration and communication
- truststoreSSO.jks → trusted certificates used for Proxy SSO (default SSO implementation)
Registry
- truststore
- truststore.jks→ trusted certificates used for PassPort client
ssofilter
- ssofilter.jks → private certificates for CAS SSO
- truststore.jks → trusted certificates for CAS SSO
Please use the method presented in Introduction to check the presence of custom certificates for each keystore that will be replaced. It’s always a good idea to backup the original files prior to replacing them.
1. Stop the Tomcat/Rule Engine Server
2. Replace the three keystore files from Product_install_folder/AIS/Tools/config/certs with the ones from the provided certs folder
3. Perform the following steps using Repository Console (../AIS/Repository/startConsole.sh or startConsole.bat)
a) Export registry file
exportRegistry <export_registry_path>
b) unregisterPassport for all applications that use PassPort
Usually, we have admin, default, designer, aistudio:
unregisterPassport admin unregisterPassport default unregisterPassport designer unregisterPassport aistudio
c) Replace <export_registry_path>/registry/truststore/truststore.jks with the one from the provided registry/truststore folder
d) Import registry:
importRegistry <export_registry_path>
4. Delete original truststore file
Delete <Product_install_dir>/AIS/Extra/PassportAM/registry/truststore directory
5. If you are using (or plan to use) the CAS SSO feature, replace ssofilter.jks and truststore.jks files from Product_Install_folder/InterPlay/war/WEB-INF with the ones from the provided ssofilter folder.
The same applies for Designer, DatastoreClient, keeping in mind the updated install path
6. Start Tomcat/Rule Engine Server
7. Validate that you can connect to the different UI as before, If not please contact Axway Support
2. Update certificates for installations with PassPort that use sample certificates combined with custom ones
You should already have the new PassPort Certificate Authority public sample certificate (attached to this KB) – PassPortCA.crt inserted in all your truststores ever since the previous one expired in 2019, issue tackled in KB Article #180329
In any case, supposing you're just using this option now, this PassPort Certificate Authority public certificate must be imported in every truststore that needs to trust sample PassPort certificates with the following command:
keytool -importcert -v -alias <alias> -file <certificate_crt> -keystore <truststore_jks>
When asked for certificate trust, answer “yes”.
It may be necessary to delete an old certificate with the same alias, in this case you can use the following command.
keytool -delete -v -alias <alias> -keystore <truststore_jks>
It’s always a good idea to backup the original files prior to updating them.
1. Stop the Tomcat/Rule Engine Server
2. Import PassPortCA.crt in Product_install_folder/AIS/Tools/config/certs truststorePassPort.jks and truststoreSSO.jks using passportca alias
3. Perform the following steps using Repository Console (../AIS/Repository/startConsole.sh or startConsole.bat)
a) Export registry
exportRegistry <export_registry_path>
b) unregisterPassport for all applications that use PassPort
Usually we have admin, default, designer, aistudio:
unregisterPassport admin unregisterPassport default unregisterPassport designer unregisterPassport aistudio
c) Import PassPortCA.crt in <export_registry_path>/registry/truststore/truststore.jks using passportca alias
d) Import registry
importRegistry <export_registry_path>
4. Delete original truststore file
Delete <Product_install_dir>/AIS/Extra/PassportAM/registry/truststore directory
5. If you are using (or plan to use) the CAS SSO feature, import PassPortCA.crt in Product_Install_folder/InterPlay/war/WEB-INF/truststore.jks using the certificateEntry property defined in properties as alias (the default value is passportssofilter)
The same applies for Designer, DatastoreClient, keeping in mind the updated install path
6. Start Tomcat/Rule Engine Server
7. Validate that you can connect to the different UI as before, If not please contact Axway Support
3. Update certificates for installations that use sample certificates in conjunction with AIS Portal (no PassPort).
1. Stop the Tomcat/Rule Engine Server
2. Replace the three jks files from Product_install_folder/AIS/Tools/config/certs with the ones from the provided certs folder
3. Start the Tomcat/Rule Engine Server
4. Specific case when running AI Suite 2.4 on Docker.
If you are running all, or some of your AI Suite 2.4 components on Docker, and have not already replaced the certificates embedded inside the image, you need to make sure that you overwrite the JKS files from inside the container with external JKS ones containing the correct certificate as external volume during your deployment implementation.
The paths for JKS inside docker image are the following:
Interplay/Datastore/Ruleserver/Designer
/usr/local/tomcat/webapps/ROOT/WEB-INF/ssofilter.jks /usr/local/tomcat/webapps/ROOT/WEB-INF/truststore.jks /usr/local/tomcat/security/keystore.jks /usr/local/tomcat/security/truststorePassPort.jks /usr/local/tomcat/security/truststoreSSO.jks
AdminUI
/usr/local/tomcat/webapps/ROOT/WEB-INF/classes/csd/truststorePassPort.jks /usr/local/tomcat/security/keystore.jks /usr/local/tomcat/security/truststorePassPort.jks /usr/local/tomcat/security/truststoreSSO.jks
Reporting/Studio
/usr/local/tomcat/security/keystore.jks /usr/local/tomcat/security/truststorePassPort.jks /usr/local/tomcat/security/truststoreSSO.jks
Please note that AI Suite 2.4 SP21 Docker image has been generated with the new sample certificates, even though we strongly recommend you to mount your own certificates instead.