KB Article #179551
Tomcat certificate expiration (31st of May)
Context:
Tomcat sample certificate provided by Axway will expire on May 31st.
Goal:
Provide updated certificates for customers who are still using Axway sample certificates, to avoid issues on production.
Customers impacted:
Customers using the Accounting Integration Suite (Interplay, Datastore and Rule Engine Server), Sentinel, Composer in production with the default Axway sample certificates.
Axway products impacted:
AISuite (2.0.0, 2.1.0), Interplay (2.2.1, 2.3.0), Datastore (2.2.1, 2.3.0) and Rule Engine Server (2.2.1, 2.3.0), Sentinel (4.1.0, 4.2.0), Composer (3.8.0).
Impacts:
- Connection to UI in HTTPS
- Deployment issue (AISuite)
- Self-registration with PassPort
Recommendation:
Axway strongly recommends replacing Axway certificates by your own certificates for security reasons.
Prerequisites in terms of how to generate custom certificates:
- Tomcat certificate must be signed by a CA with at least SHA-256 signature algorithm.
- RSA key length must be 2048 (less is insecure; more can create performance problems).
- Subject DN (Organization, OU, Country, etc.) -> client’s own information.
- Extensions (what we are using right now):
- extendedKeyUsage=serverAuth
- keyUsage=digitalSignature, nonRepudiation, keyEncipherment
- basicConstraints=CA:FALSE
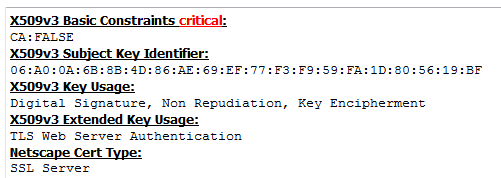
- Expiration date – no more than 2-3 years (otherwise security audit related issues can occur).
Regarding the CA :
- Can be self-signed, which can be an intermediary CA signed by another CA. The cheapest method is to have a self-signed one (with SHA-256).
- CA specifics: basic constraint isCA=TRUE (basicConstraints=critical;CA:TRUE) and key usage: keyUsage=keyCertSign, cRLSign:
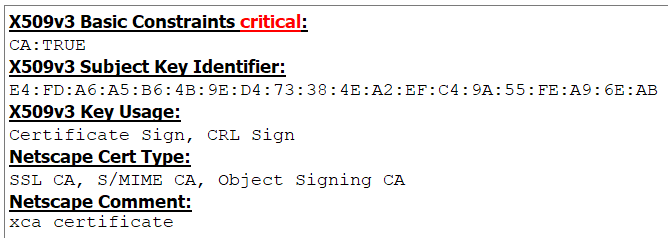
- Recommended key length: 4096 (being a CA).
Steps:
1. Check that you are using Axway certificates and the expiration date
You can use the keytool.exe provided in our embedded java.
keytool.exe -v -list -keystore keystore.jks
No password is required
Alias name: tomcat
Creation date: 31 mai 2016
Entry type: PrivateKeyEntry
Certificate chain length: 3
Certificate[1]:
Owner: CN=Tomcat, O=Axway, C=FR
Issuer: CN=PassPort SSO CA, O=Axway, C=FR
Serial number: 1d
Valid from: Tue May 31 11:44:00 CEST 2016 until: Thu May 31 11:44:00 CEST 2018
Certificate fingerprints:
MD5: 5D:89:06:85:A0:24:1B:6E:49:3B:81:38:F3:C7:90:1C
SHA1: B4:F3:D8:09:48:33:4F:C0:96:BC:34:30:3B:1B:D5:85:5F:6E:F8:7E
SHA256: 81:2B:39:95:B0:2A:0F:02:19:F6:AC:0B:D8:D4:2B:32:F6:4E:09:E2:15:
67:D5:19:34:04:B5:E9:A9:AD:D2:20
Signature algorithm name: SHA256withRSA
Version: 3
2. Replacement procedure
Although Axway is strongly advising against the usage of the sample certificate (at least for production purposes) we’re going, nevertheless, to present a procedure for changing this certificate since there are multiple entities (Support, PSO, etc) that are using sample certificates for testing purposes.
2.1. AISuite (Datastore, Interplay and Rule Engine Server)
For AISuite 2.0.0 and 2.1.0
Please refer to the following article and use the 2018 files:
https://support.axway.com/en/articles/article-details/id/176490
For InterPlay, Datastore and Rule Engine Server 2.2.1 and above
Please refer to the attached
document: AIS Tomcat certificate change procedure.docx
Sample Axway certificates
Axway provides sample certificates for testing purposes. They can be found attached:
- PassPortCAs
- PassPort_SSO_CA.crt – signed with SHA-1
- PassPort_SSO_CA_1.crt – signed with SHA-256
- PassPortCA.crt
- ssofilter
- ssofilter.jks
- Tomcat_2017_2019
- keystore_SSOCA-SHA1.jks
- keystore_SSOCA-SHA2.jks - signed with SHA-256
2.2. Sentinel
For Sentinel 4.1.0:
- The updated certificates are included in Sentinel 4.1.0 SP7
- You can also manually replace the certificate by using the procedure described here: https://support.axway.com/en/articles/article-details/id/176490/do/search
For Sentinel 4.2.0:
- The updated certificates are included in Sentinel 4.2.0 SP10
- You can also manually replace the certificate by copying the provided jks files in the directory ../<Sentinel>/conf/security
2.3. Composer
Replace the file called keystore.jks found under ../<INSTALL>/Common/config/certs with the attached file or use the procedure described in the article: https://support.axway.com/en/articles/article-details/id/176490/do/search