KB Article #180893
Supported SSH Message Authentication Codes (MAC) in SecureTransport 5.3.3
Problem
The official documentation for SecureTransport 5.3.3 does not list the complete list of supported SSH MACs when SecureTransport is acting as a client (i.e. performing a Server Initiated Transfer, trying to connect to a remote SSH server). This article provides the full detail list of supported MACs.
Resolution
Newer versions, starting with SecureTransport 5.3.6, do provide the option to view and edit the currently supported list of MACs trough their Server Configuration page - Ssh.SIT.AllowedMacs. However, this option is not available in SecureTransport 5.3.3 and this makes finding the list of supported MACs a bit difficult.
The following is the list of supported SSH MACs when SecureTransport 5.3.3 is acting as a client (as per the J2SSH/Maverick library which ST implements):
HMAC_SHA1 HMAC_SHA1_ETM HMAC_SHA1_96 HMAC_MD5 HMAC_MD5_ETM HMAC_MD5_96 HMAC_SHA256 HMAC_SHA256_ETM HMAC_SHA256_96 HMAC_SHA512 HMAC_SHA512_ETM HMAC_SHA512_96 HMAC_RIPEMD160 HMAC_RIPEMD160_ETM
You can also see the full list when SecureTransport establishes a successful connection (and a transfer) to a remote SSH server within the transfer's record in File Tracking page:
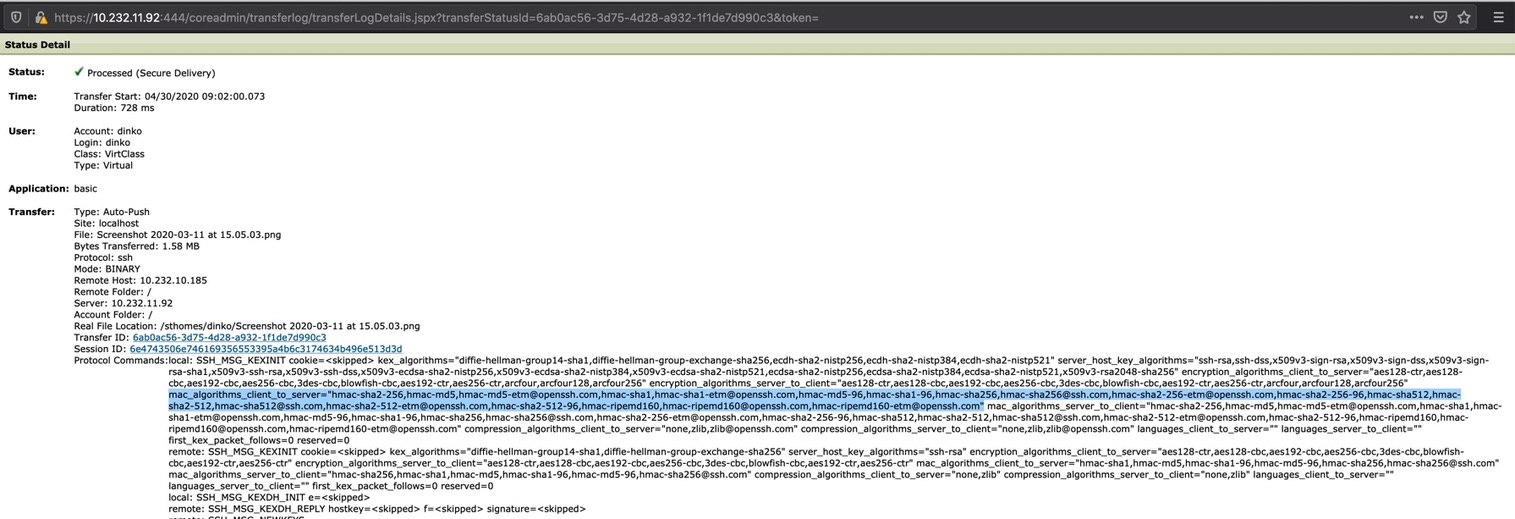
local: attributes, in particular the mac_algorithms_client_to_server= line we can see the full list:
mac_algorithms_client_to_server="hmac-sha2-256,hmac-md5,hmac-md5-etm@openssh.com,hmac-sha1,hmac-sha1-etm@openssh.com,hmac-md5-96,hmac-sha1-96,hmac-sha256,hmac-sha256@ssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-256-96,hmac-sha512,hmac-sha2-512,hmac-sha512@ssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha2-512-96,hmac-ripemd160,hmac-ripemd160@openssh.com,hmac-ripemd160-etm@openssh.com"
Additional information about FIPS transfer mode
In some occasions, it might be needed to enable only FIPS transfer mode in the Transfer Site (i.e. select the Enable FIPS Transfer Mode option). In this case the list of SSH MACs will be limited to HMAC-SHA1 only (as per the Administrator Guide, page 752).