KB Article #181185
ONEDRIVE: Configuring the OneDrive connector for SecureTransport
Overview
The OneDrive Connector enables Axway SecureTransport (ST) to exchange files with OneDrive. It is deployed as a Transfer Site plugin to an existing ST installation. Once deployed, it provides a new Protocol - OneDrive to the list of available protocols in the Add New Transfer Site page for User Accounts.
An introduction to general Transfer Site configuration is available in the SecureTransport’s Administration Guide under section Manage accounts: Transfer sites. [ST 5.5 Administrator Guide] [ST 5.4 Administrator Guide]
Prerequisites
A Microsoft Azure account with an active subscription
An Azure AD tenant
Access to Azure Active Directory
Installed SecureTransport 5.4 with Patch 35 or higher
Download
The OneDrive Connector for SecureTransport installation package can be downloaded from the AMPLIFY Repository.
Installation
To install the OneDrive Connector for SecureTransport, perform the following steps on all SecureTransport Server nodes:
Delete the following files/folders associated with the previous version of this step (if they exist):
<FILEDRIVEHOME>/plugins/transferSites/axway-site-onedrive.jar<FILEDRIVEHOME>/plugins/transferSites/axway-site-onedrive
The existing configurations in ST will be preserved.
Extract the securetransport-plugins-site-onedrive-<plugin_version>.zip into <FILEDRIVEHOME>/plugins/transferSites
Restart all SecureTransport services
Setup Azure application and permissions
Register a new application
In order to access OneDrive REST endpoints exposed in Microsoft's Graph API, an application with specific permissions must be created.
Log into https://portal.azure.com using either a work or school account or a personal Microsoft account.
If your account gives you access to more than one tenant, select your account in the upper right corner. Set your portal session to the Azure AD tenant that you want.
Go to Azure Active Directory. Under Manage, select App registrations.
Click New Registration.
Specify application name and choose account types that can use the application:
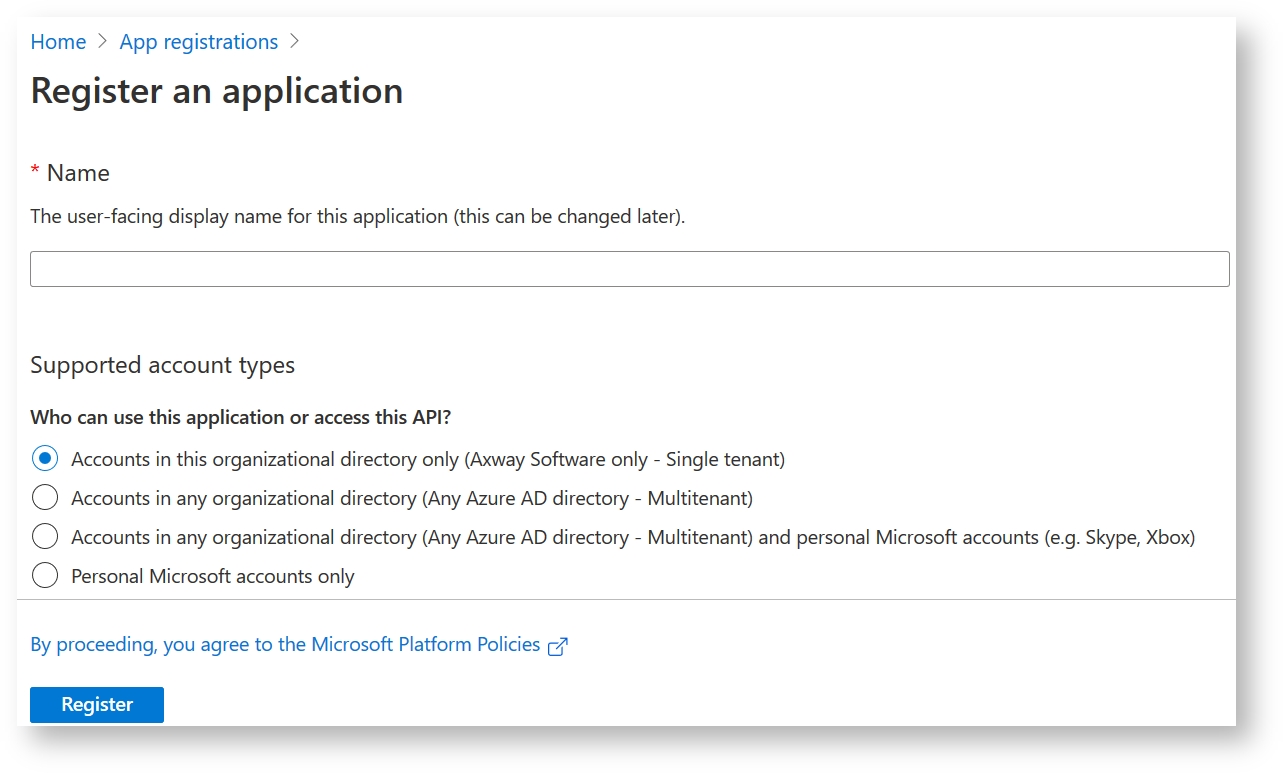
Register the application
Add credentials to the application
In most cases, the application must have a client secret configured in order to make API requests. The client secret is a secret string (can be referred to as application password) that the application uses to prove its identity.
To add a client secret:
From the app Overview page, select the Certificates & secrets section.
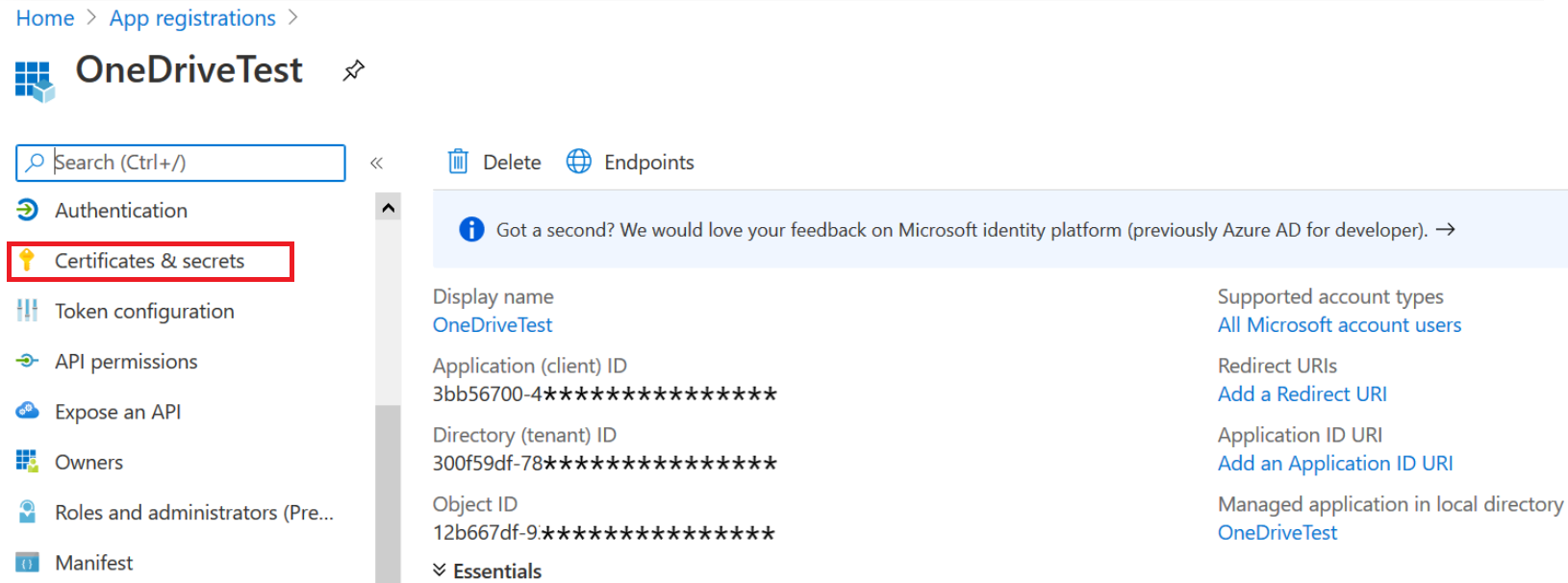
Select New client secret.
Add a description for your client secret.
Select a duration.
Select Add.
After you save the configuration changes, the right-most column will contain the client secret value. Be sure to copy the value for use in your client application code as it's not accessible once you leave this page.
If the authentication flow is Client Credentials or the application is a confidential client, the client secret is required, otherwise it is optional.
Setup Permissions
After an application is registered in Azure Portal App Registrations, the required permissions to access the web API must be assigned to that application.
You can select from two types of permissions for each web API:
Application permissions. The client application needs to access the web API directly as itself, without user context. This type of permission requires administrator consent. This permission is relevant for Client Credentials flows.
Delegated permissions. The client application needs to access the web API as the signed-in user, but with access limited by the selected permission. This type of permission can be granted by a user, unless the permission requires administrator consent. This permission is relevant for Resource Owner flows.
To add permissions to access resource APIs from your client application:
Open the application settings and go to API Permissions.
Click Add Permission.
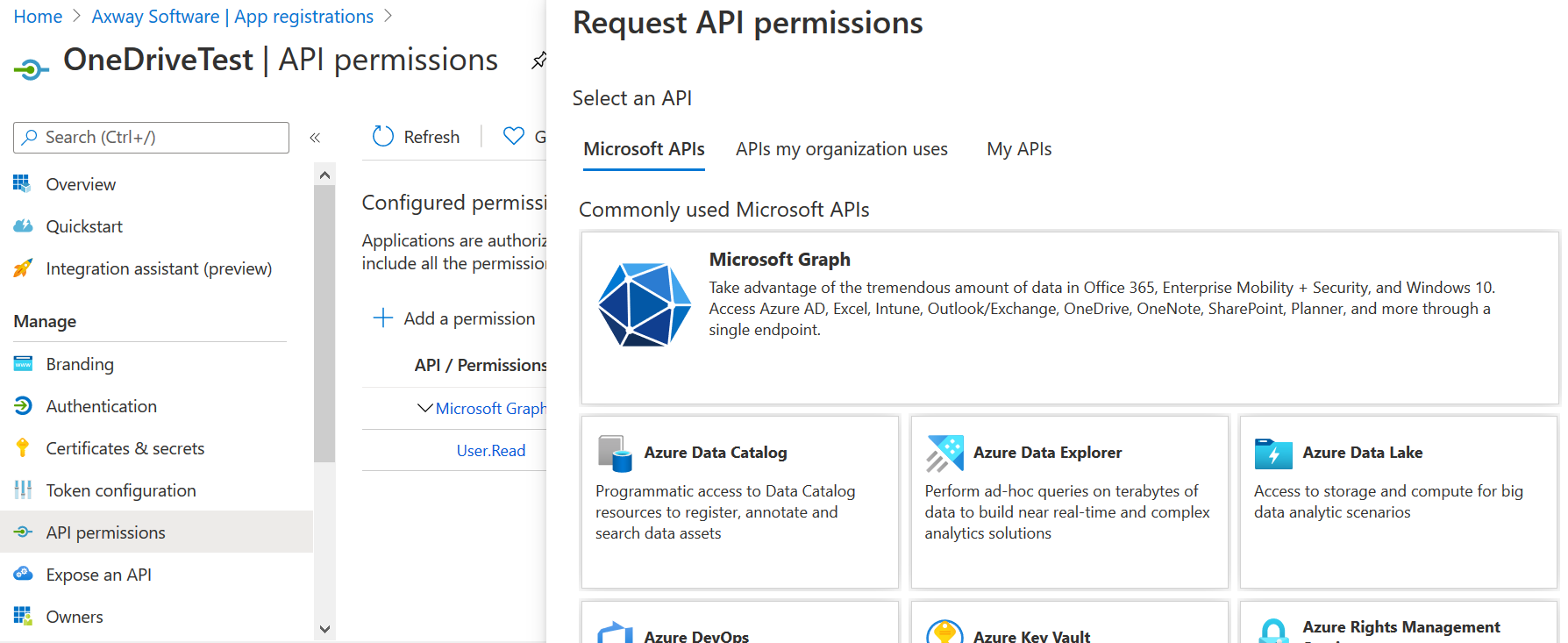
Select Microsoft Graph.
In case of Resource Owner authentication flow select the following Delegated permissions: Files.ReadWrite.All, offline_access
In case of Client Credentials authentication flow select the following Application permissions: Files.ReadWrite.All
Click Add Permissions.
After the required Admin consent has been granted by an Azure AD administrator (on behalf of the user for delegated permissions), the application will be available for use in the MS Graph APIs.
Configure a Transfer Site in SecureTransport
Create a Transfer Site under an existing User Account. Choose OneDrive from the Transfer Protocol dropdown menu.
Connection settings: All connection credentials can be found in Azure Portal → App Registrations → App Overview page.
Client ID - Set the Application ID assigned by the app registration portal.
Client Secret - Set the Client Secret created for the application.
Tenant - Set the Tenant ID of the application
Endpoint - Choose the national cloud in which the application is deployed. (Global, China, Germany or UsGovernment)
Authentication Flow - The supported authentication flows are Resource Owner and Client Credentials.
In case of Resource Owner authentication flow: Set Microsoft Azure account's Username and Password.
In case of Client Credentials authentication flow: Set a valid user, group or drive Object ID (the ID of the object in Azure AD which drive will be accessed).
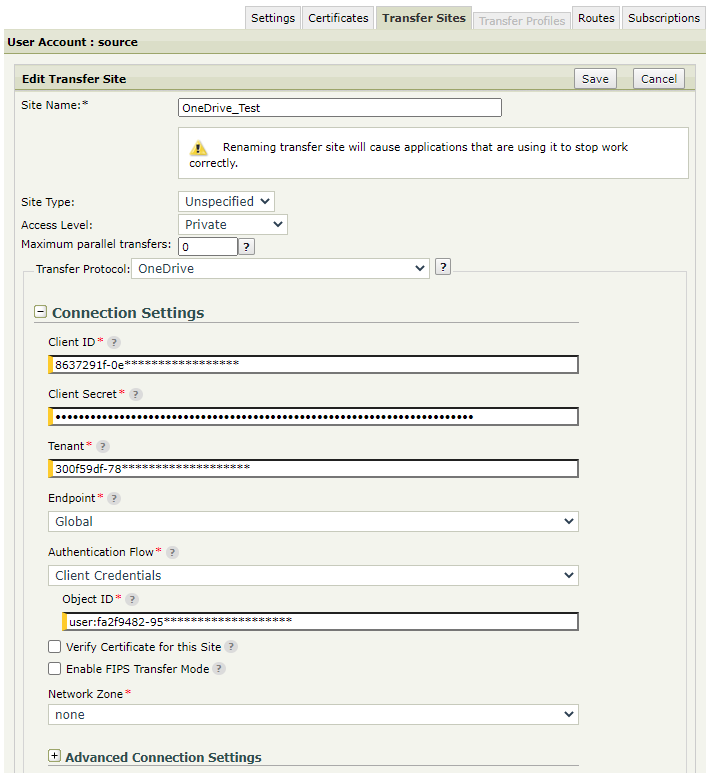
Download/Upload settings: Configure the download and upload settings as for a regular Transfer site, as well as any needed PTA settings.
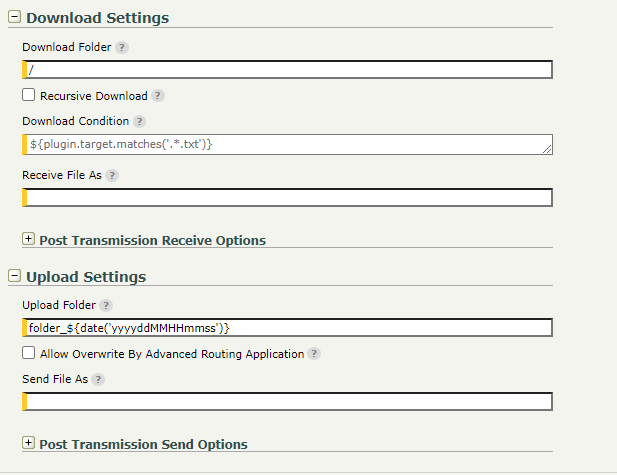
Test the Setup
Server Initiated Pull by ST
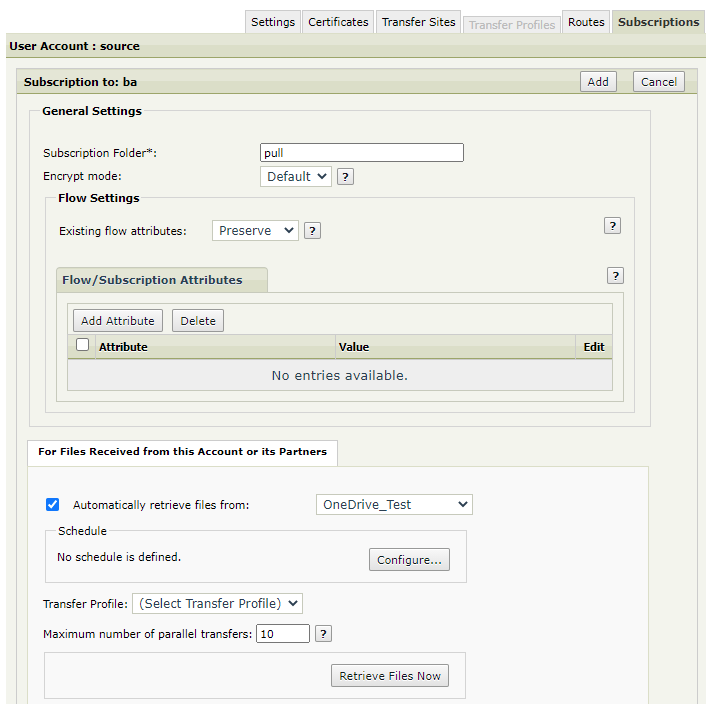
Create a Subscription to a Basic Application (BA).
In the For Files Received from this Account or its Partners section, select Automatically retrieve files from and select the OneDrive Transfer Site from the drop-down.
Set a schedule or alternatively, use the Retrieve Files Now button after the Subscription was saved (i.e. save the Subscription, re-open it and then use the button).
[optional] Under For Files Sent to this Account or its Partners, select Send Files Directly To and select a different Site where the test file should be sent to (local or remote location) after it's pulled from OneDrive.
Save the Subscription.
Place a test file in OneDrive in the folder that was defined under "Download Settings" of the OneDrive Site in ST.
Wait for the scheduler to trigger or use the Retrieve Files Now button in the Subscription.
Go to Operations → File Tracking → Show Advanced Search, then filter by "Protocol: onedrive" and make sure each of the transfers succeeded with green check Transfer Status icon.
Server Initiated Push from ST
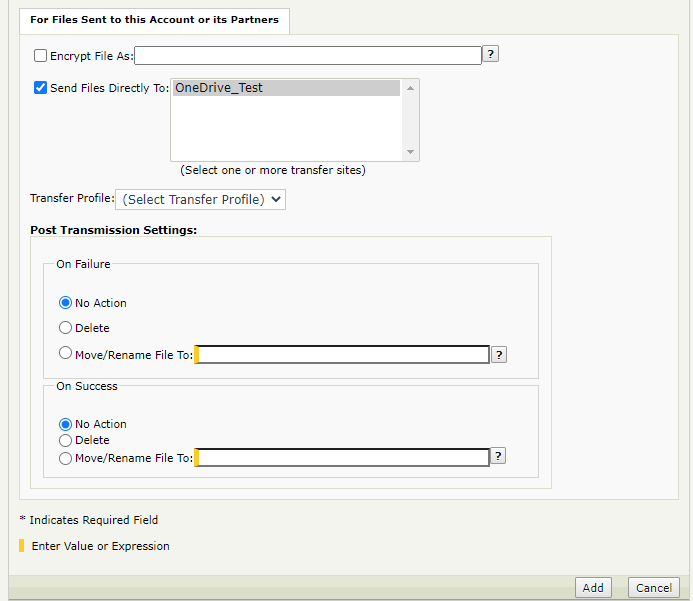
Create another Subscription to a Basic Application (BA).
Under For Files Sent to this Account or its Partners, select Send Files Directly To and select the OneDrive Transfer Site.
Login to ST with the user account and upload a test file in the Subscription Folder. Wait for a few seconds.
Go to Operations → File Tracking → Show Advanced Search, then filter by "Protocol: onedrive" and make sure each of the transfers succeeded with green check Transfer Status icon.
If all have succeeded, go to OneDrive and check the folder defined under "Upload Settings" of the OneDrive Site in ST. The file should be there.
Troubleshooting and Notes
To enable extended debug logging, edit the <FILEDRIVEHOME>/conf/tm-log4j.xml config file. Find the com.axway.st.plugins.site logger element and set its level value to DEBUG.
The OneDrive Transfer Site can be configured using the /sites ST Admin REST API endpoint. The REST API definition of the OneDrive Transfer Site is available in Swagger YAML file format under <FILEDRIVEHOME>/plugins/transferSites/axway-site-onedrive.
For a complete list, refer to the section Known Issues and Limitations in the README.md file included in the OneDrive Connector archive.