KB Article #181873
CERTIFICATES: Extend the validity of a certificate signed with the ST internal CA
Before you begin
In the below examples, the following notations and names are used:
$FILEDRIVEHOME is the full system path to the installation directory of SecureTransport. The placeholder should be replaced by the full system path before using it in commands.
EXPIRED-CERT.p12 is the exported current (expiring/expired) certificate from SecureTransport (including the private key).
Resolution
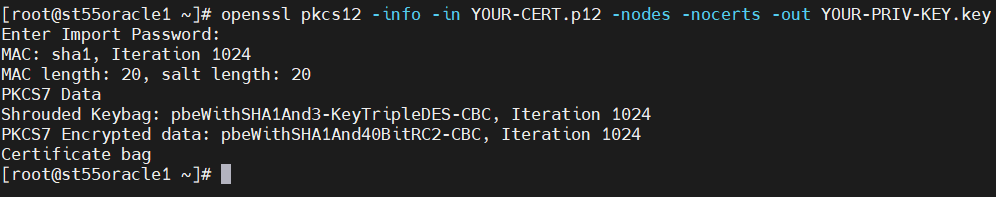
1. Export the private key from your current certificate:
openssl pkcs12 -info -in EXPIRED-CERT.p12 -nodes -nocerts -out YOUR-PRIV-KEY.key
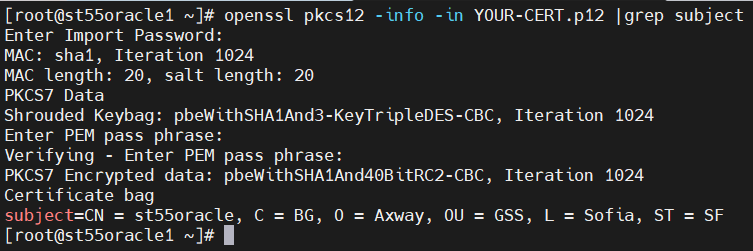
2. Get the current information from your certificate (CN=; OU=; etc.):
openssl pkcs12 -info -in EXPIRED-CERT.p12 |grep subject
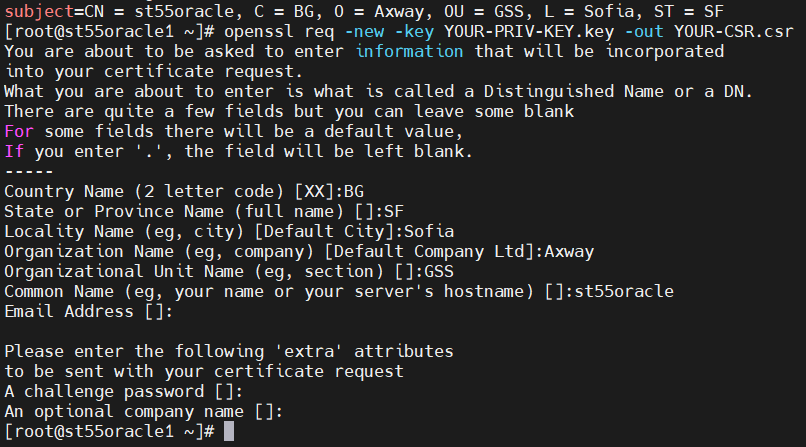
3. Generate a new CSR for the new certificate and fill up the information gathered from Step 2:
openssl req -new -key YOUR-PRIV-KEY.key -out YOUR-CSR.csr
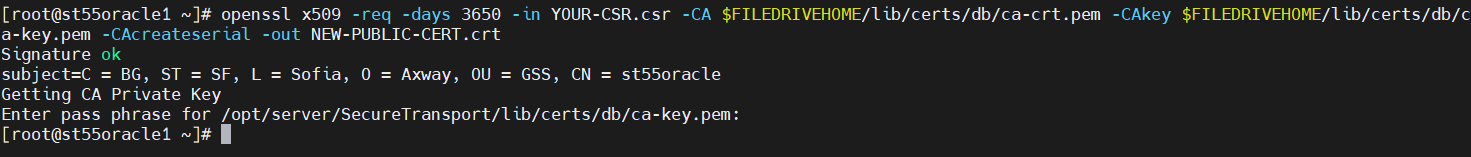
4. Extend the validity of the certificate with N number of days (must be less than what is left for the current Internal CA). In the example it is extended by 3650 days:
openssl x509 -req -days 3650 -in YOUR-CSR.csr -CA $FILEDRIVEHOME/lib/certs/db/ca-crt.pem -CAkey $FILEDRIVEHOME/lib/certs/db/ca-key.pem -CAcreateserial -out NEW-PUBLIC-CERT.crt
5. Generate the new PKCS12 capsule that you will import in the ST server:
openssl pkcs12 -export -out NEW-CERT.p12 -inkey YOUR-PRIV-KEY.key -in NEW-PUBLIC-CERT.crt
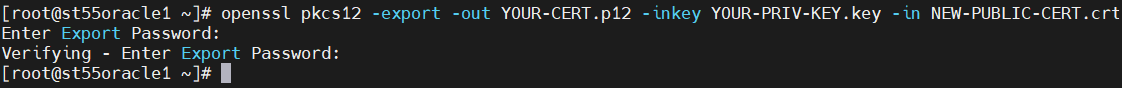
When asked, provide a password for the new certificate. It must be at least 8 characters long.
The resulting NEW-CERT.p12 is the renewed/extended certificate and can be imported into ST. This new certificate will have the same fingerprint and will be valid and chained to a trusted root. You can now delete the .p12, .key and .csr files.