KB Article #182281
SECURITY: Obtain the list of client-proposed ciphers, MACs and KEX algorithms for SSH connections
Problem
In general, SecureTransport does not log the presented ciphers/MACs/KEXs from client-initiated SSH connections. Still, for the purpose of a security audit in some cases it is beneficial to obtain the list of security parameters proposed by the clients. This article with provide instructions how to do this.
Resolution
Add a new logger on DEBUG for the com.tumbleweed.st.server.sshd.logging.SSHDLoggingListener class in the $FILEDRIVEHOME/conf/sshd-log4j.xml file.
IMPORTANT NOTE: This will produce a large amount of Server Logs records for each SSH connection attempt. On highly loaded environments this will lead to congestion of the Server Log in the Admin UI and an increase in size of the related database tables. It is recommended that the new Logger is pointed to a file log Appender.
Add a file log Appender below the default Appenders in the file (optional)
If you do not want to store the records in a file, but leave them being recorded in the database instead (and visible in the Admin UI), skip this step.
<File append="true" fileName="/opt/Axway/SecureTransport/var/logs/sshd-client-params.log" name="SSHClientParamsLog">
<PatternLayout pattern="%d{ISO8601} [%t] %p %c %equals{%x}{[]}{} - %m%n%ex"/>
</File>
Add a new Logger below the default Loggers in the file
If you skipped the previous step with the file Appender, change the <AppenderRef ref="SSHClientParamsLog"/> to <AppenderRef ref="ServerLog"/> in the code below.
<Logger additivity="false" level="DEBUG" name="com.tumbleweed.st.server.sshd.logging.SSHDLoggingListener">
<AppenderRef ref="SSHClientParamsLog"/>
</Logger>
Restart the SSH service
After the change is applied, the client-proposed connection parameters will be stored in the file log specified in the Appender above.
In case you have opted to store the records in the database (i.e. no file Appender was added and the Logger was pointed to the ServerLog appender), they will be visible in the Server Log page of the Admin UI. Due to the sheer amount of records produced, it might be difficult to pin-point the connection parameters, so an easy way to filter the records is to run a search for the phrase EVENT_KEY_EXCHANGE_INIT in the Message field and then open the record's details. You will see something like this:
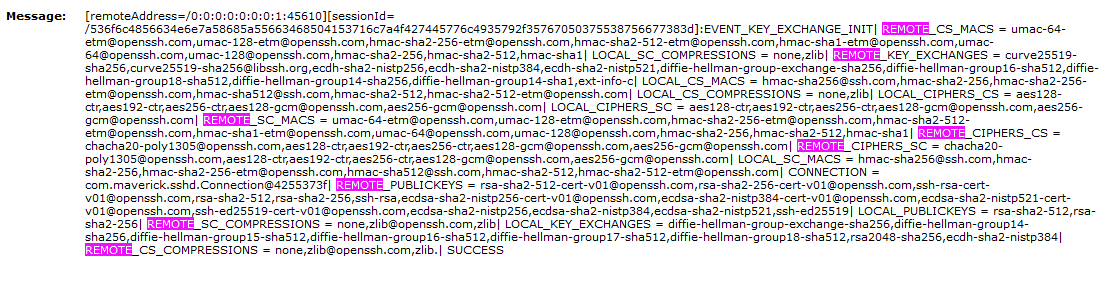
The client-proposed connection parameters will be visible in the log message's details