KB Article #180611
AZURE: Configuring the Azure Blob Storage connector for SecureTransport
Overview
The Azure Blob Connector enables Axway SecureTransport (ST) to exchange files with existing Azure Storage account with Blob service enabled. It is deployed as a Transfer Site plugin to an existing ST installation. Once deployed, it provides a new protocol - Azure Blob Storage - to the list of available protocols in the Add New Transfer Site page for User Accounts.
An introduction to general Transfer Site configuration is available in the SecureTransport’s Administration Guide under section Manage accounts: Transfer sites. [ST 5.5 Administrator Guide] [ST 5.4 Administrator Guide]
Prerequisites
A Microsoft Azure account with an active subscription
Access to Azure Resource Group and Storage account
Download
The Azure Blob Storage Connector for SecureTransport installation package can be downloaded from the AMPLIFY Repository.
Installation
To install the Azure Blob Storage Connector for SecureTransport, perform the following steps on all SecureTransport Server nodes:
Delete the following files/folders associated with the previous version of this step (if they exist):
<FILEDRIVEHOME>/plugins/transferSites/axway-site-azure-blob.jar<FILEDRIVEHOME>/plugins/transferSites/axway-site-azure-blob
The existing configurations in ST will be preserved.
Extract the securetransport-plugins-site-azureblob-<plugin_version>.zip into <FILEDRIVEHOME>/plugins/transferSites.
Restart all SecureTransport services.
Connect with Identity Service Principal
Log into https://portal.azure.com using either a work or school account or a personal Microsoft account.
Create an app from App Registrations page. More information on creating can be found at: https://learn.microsoft.com/en-us/azure/purview/create-service-principal-azure
Collect the following App Registration details needed for establishing a connection
Application (client) ID
Directory (tenant) ID
Client credentials - either a Secret or a client Certificate
Go to Storage Accounts and open the storage account that you need to access.
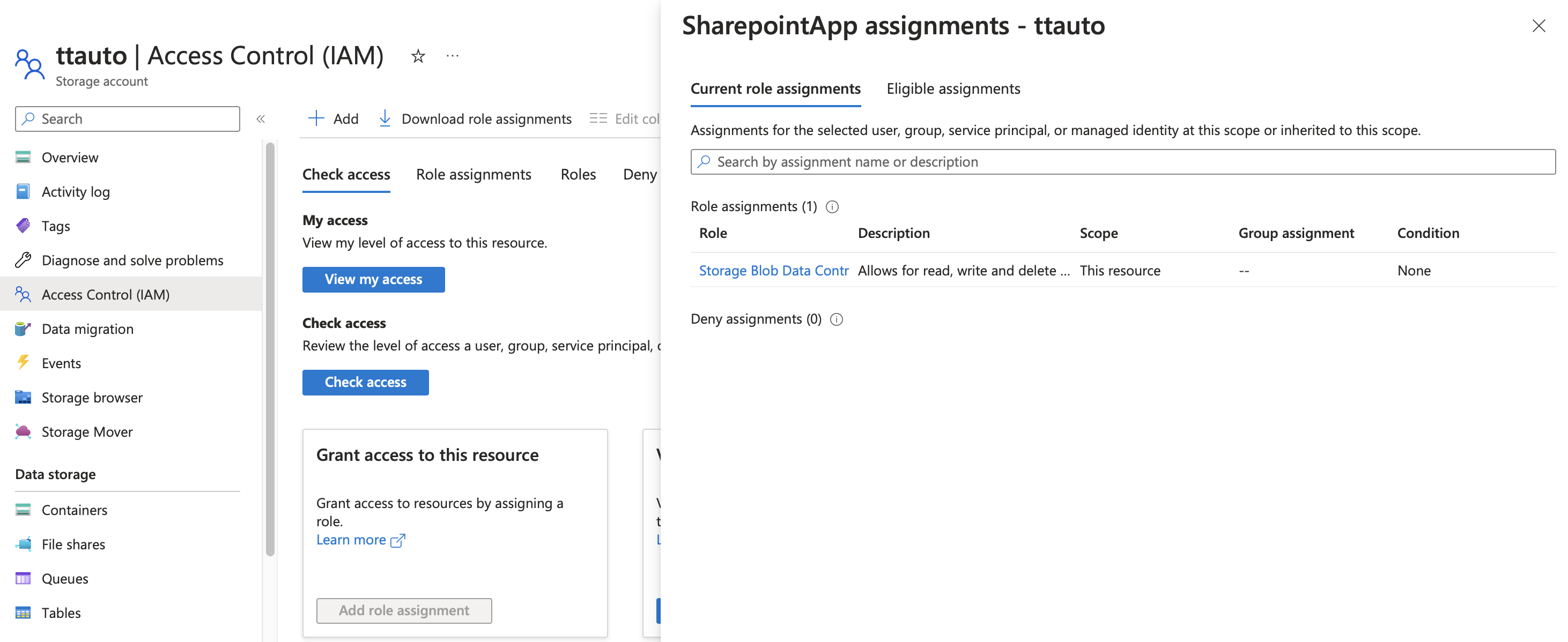
Navigate to the Access Control (IAM) page for the storage account and open the Grant access to this resource menu
Assign an access role to the App Registration created earlier with sufficient privileges - e.g. Storage Blob Data Contributor
Create a Transfer Site with Service Principal in Secure Transport
Create a Transfer Site under an existing User Account. Choose Azure Blob Storage from the Transfer Protocol dropdown menu.
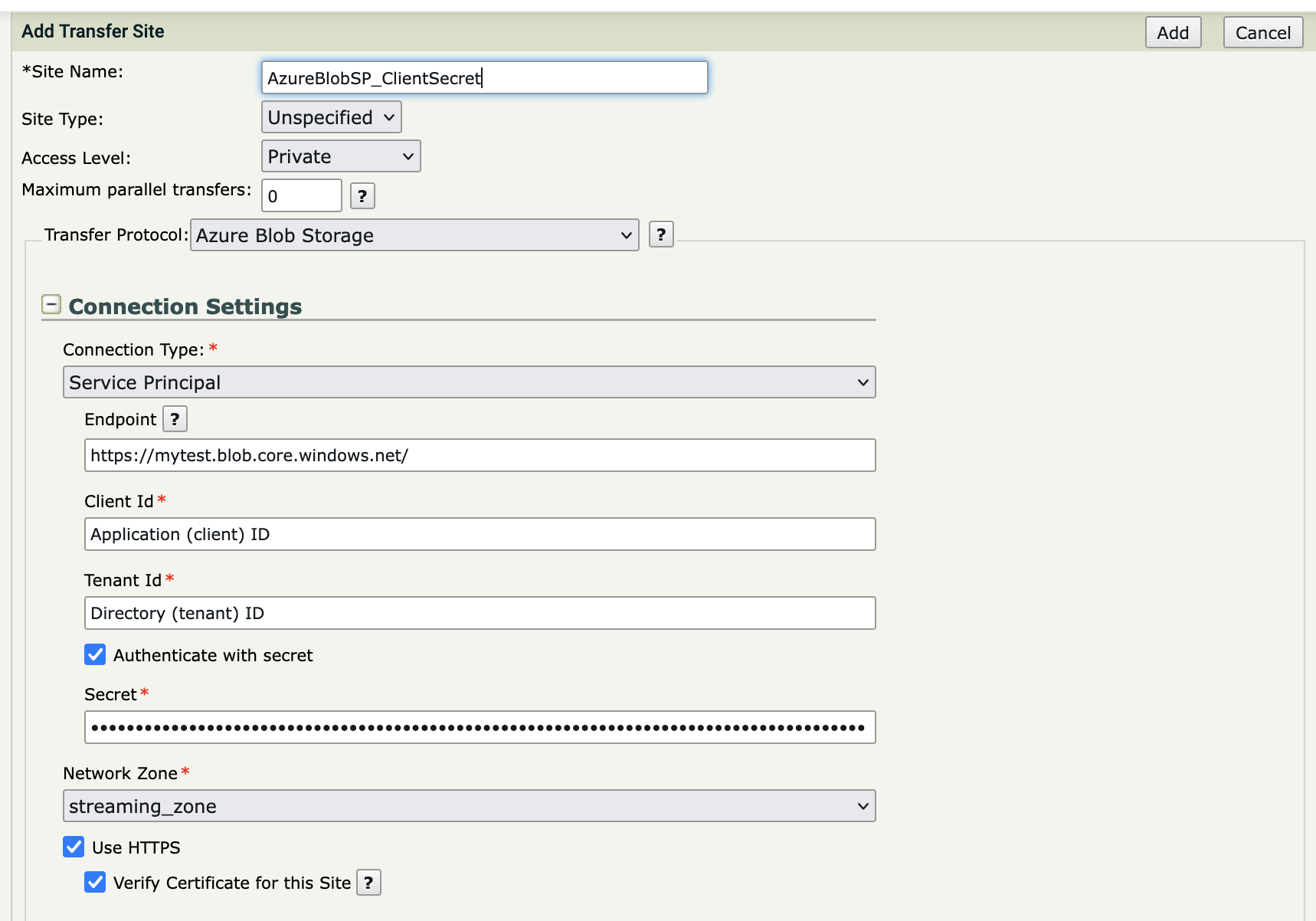
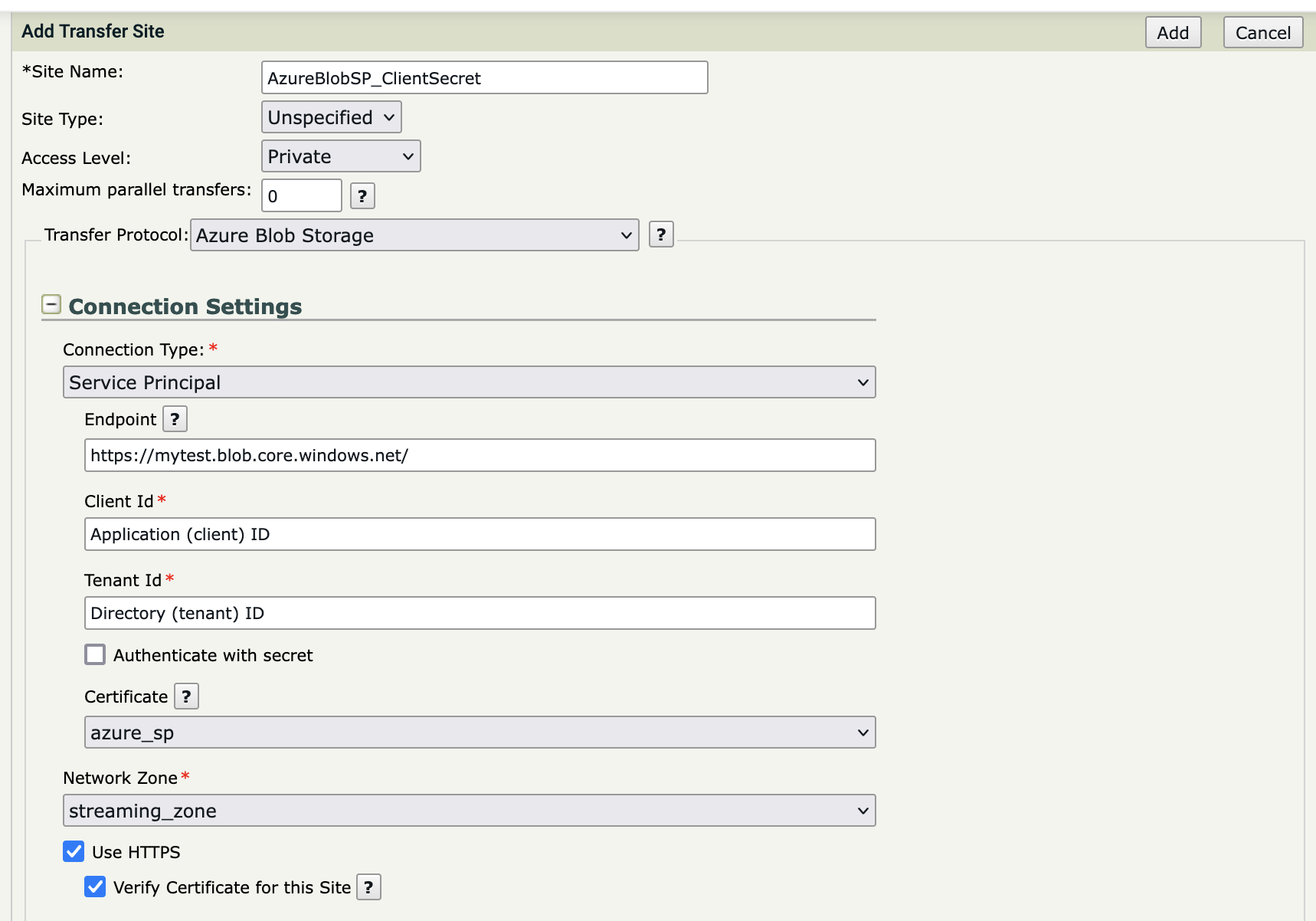
Select Service Principal for Connection Type
Enter the details for your Azure Blob Container.
- Client Secret
- Certificate
Connect with Connection String Authentication
Get a Connection String
Log into https://portal.azure.com using either a work or school account or a personal Microsoft account.
Go to Storage Accounts and open the storage account you want access to.
Select Access keys under Settings, click Show keys and copy one of the two Connection strings.
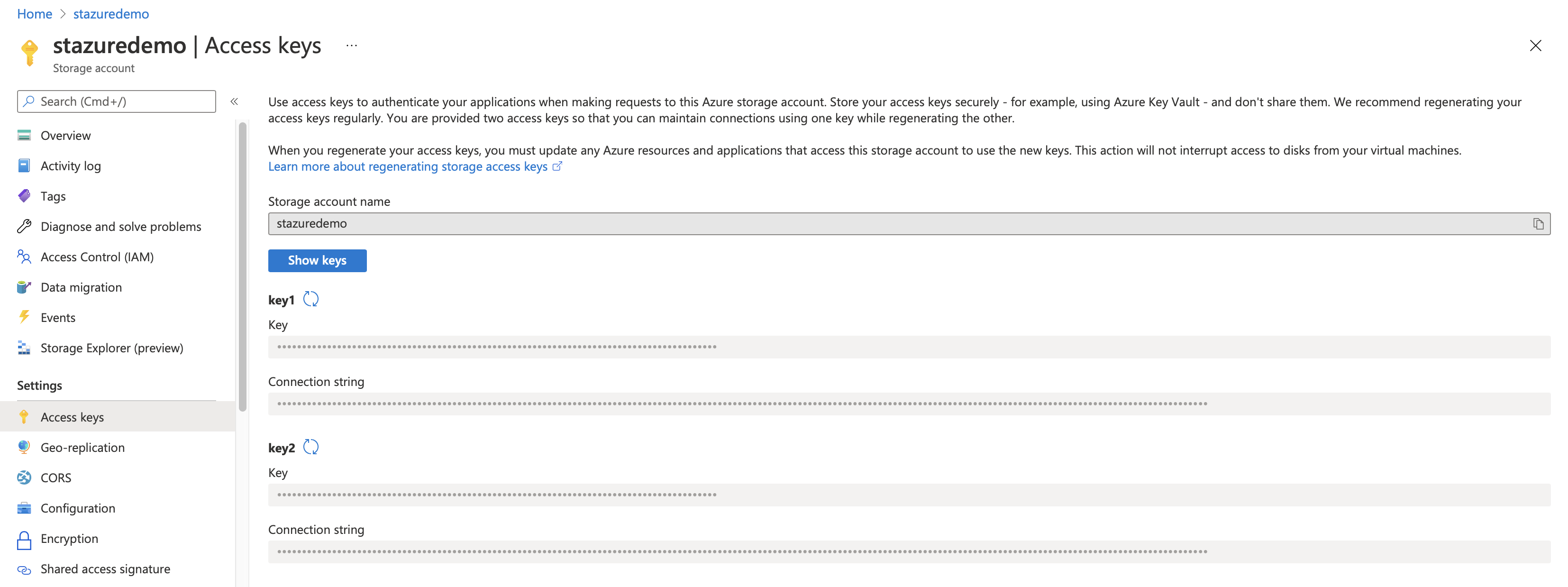
Get the Connection String from this page
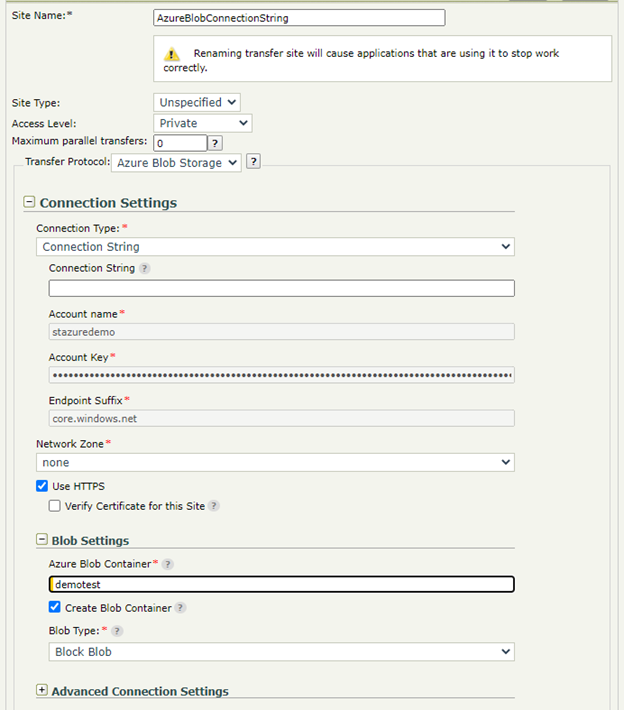
Create a Transfer Site with Connection String in Secure Transport
Create a Transfer Site under an existing User Account. Choose Azure Blob Storage from the Transfer Protocol dropdown menu.
Select Connection String for Connection Type, and paste the copied Connection String in the field. After a proper Connection String is provided, the Account Name, Account Key and Endpoint Suffix fields should be extracted from the Connection String and auto-populated (the Account Key is sensitive data, so it is hidden).
Enter the details for your Azure Blob Container.
Download/Upload settings: Configure the download and upload settings as for a regular Transfer site, as well as any needed PTA settings.
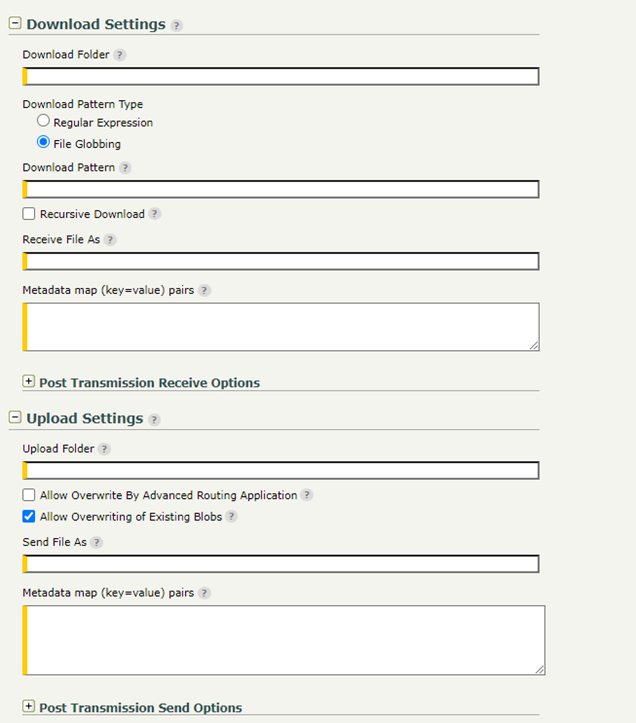
Note: If the Download Folder field is empty, the container's root directory will be used.
Connect with Shared Access Signature (SAS) Authentication
There are 5 types of SAS - Account level, Service level, User delegation, Container level and Blob level. The Container and Blob levels of SAS are discussed below.
Log into https://portal.azure.com using either a work or school account or a personal Microsoft account.
Get a Container level SAS
Go to Storage Accounts and open the storage account you want access to.
Select Shared Access Signature under Settings.
Select Container in Allowed resource types. You can edit the allowed permissions and the Start/Expiry dates.
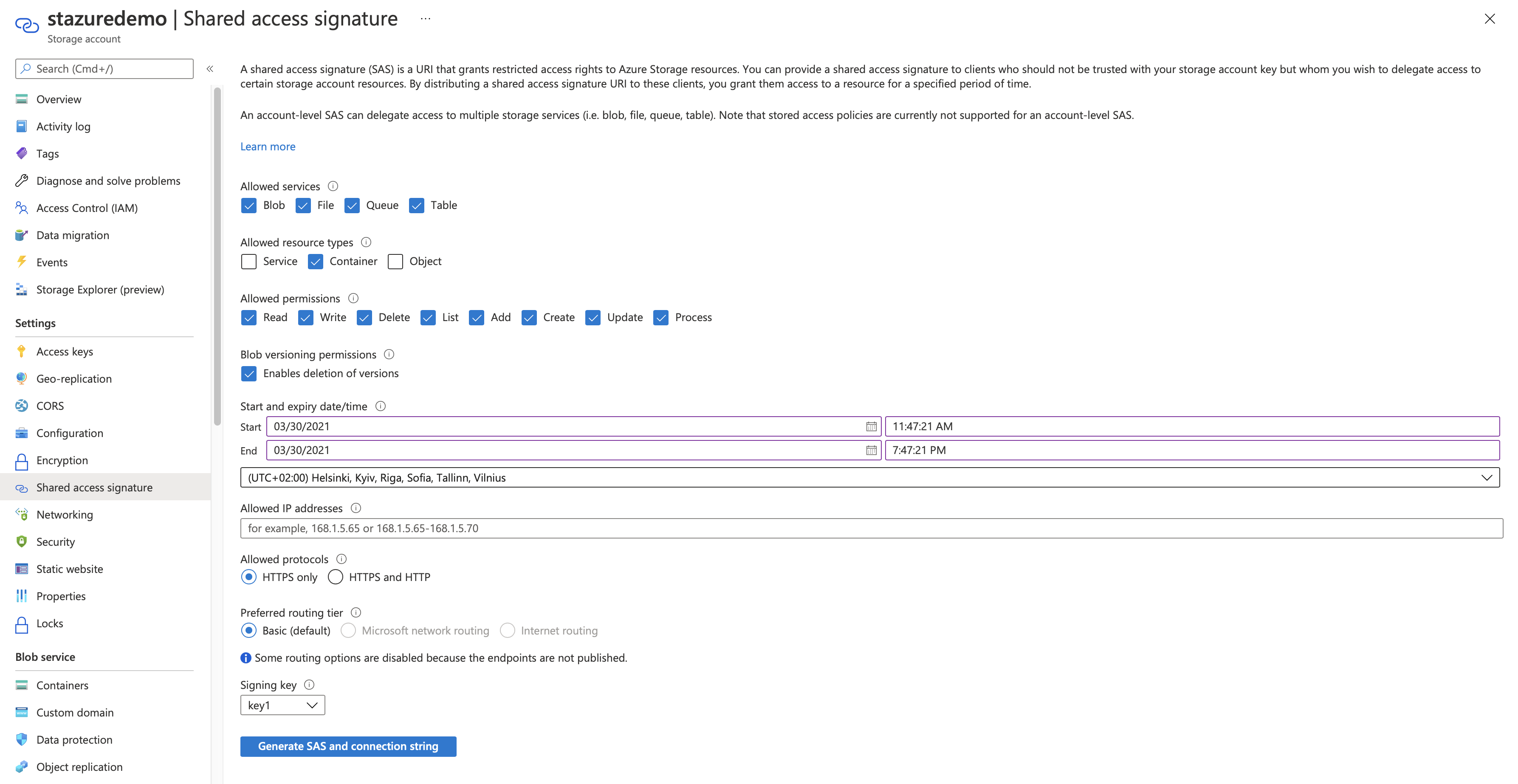
Generate a Container level SAS
Click Generate SAS and connection string and copy the Blob service SAS URL.
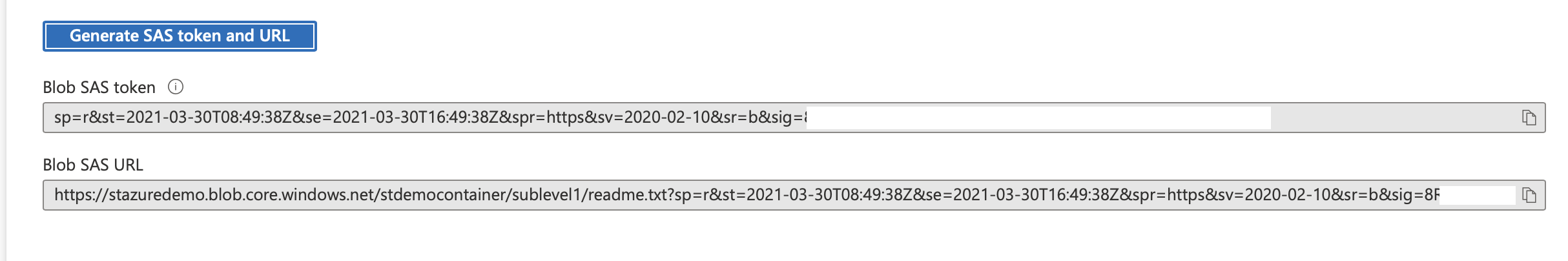
Get a Blob level SAS
Go to Storage Accounts and open the storage account you want access to.
Select Storage Explorer (preview) and right click the blob you want access to.
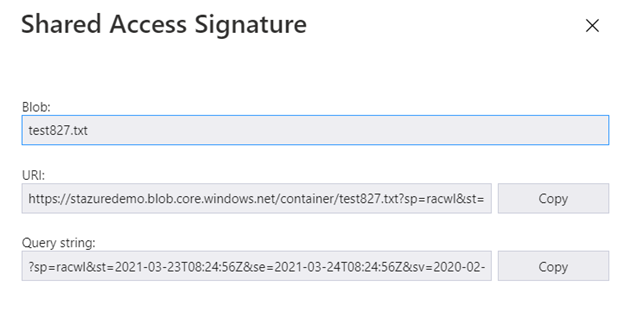
Select Get Shared Access Signature. You can edit the allowed permissions and the Start/Expiry dates.
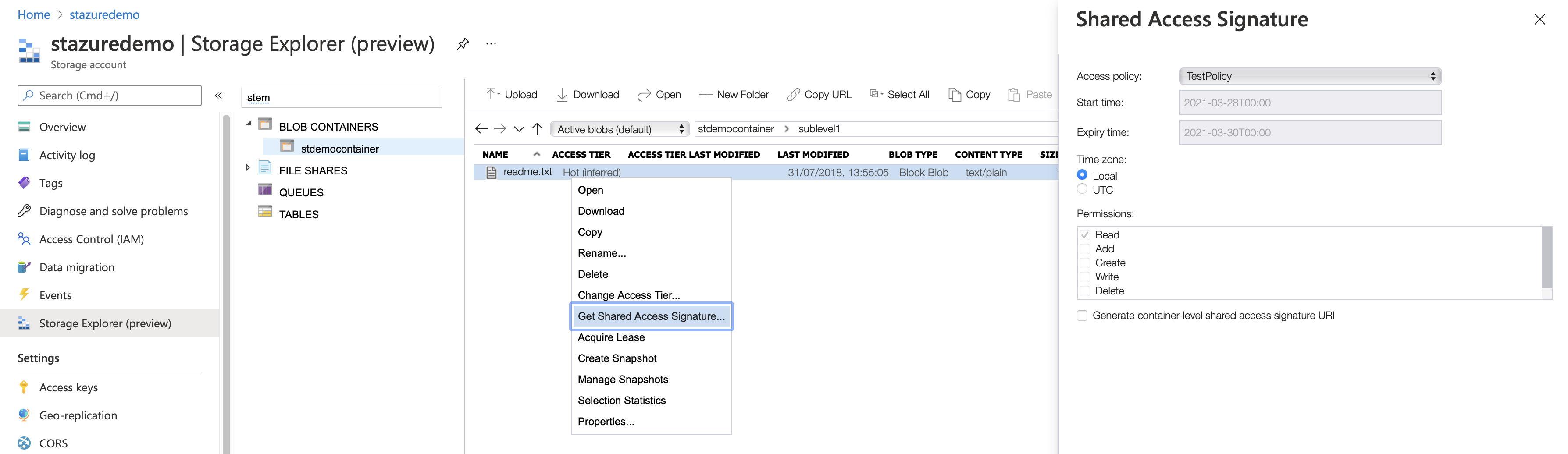
Select Create and copy the URI.
Generate SAS with Access Policy
Go to Storage Accounts and open the storage account you want access to.
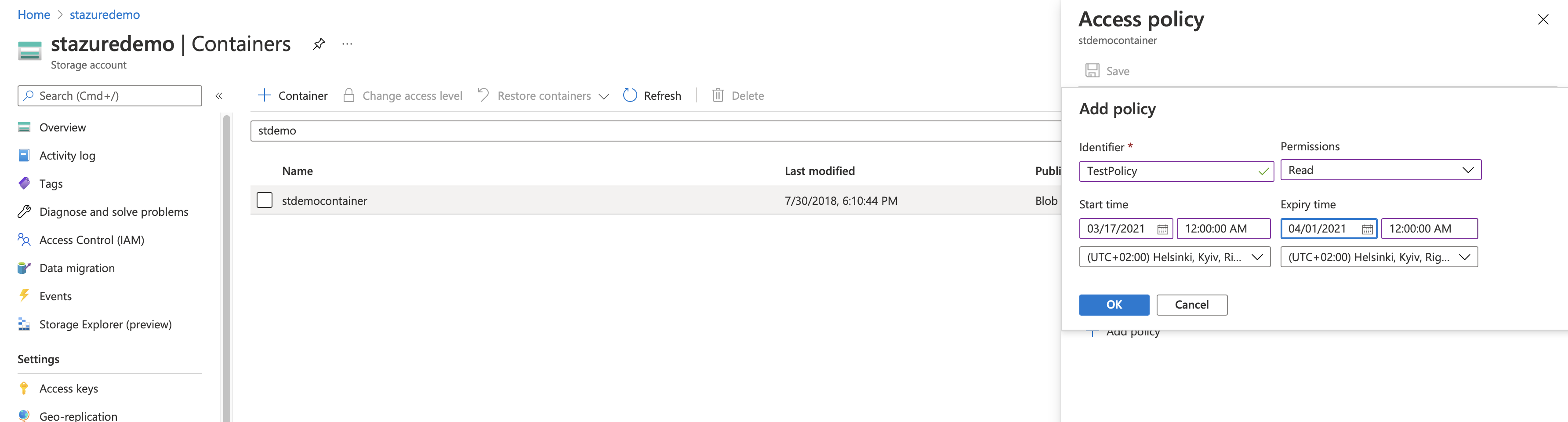
Select Containers under Blob Service and right click the container you want to generate Access Policy for.
Select Access Policy and on the Access Policy window select Add policy and create one.
Select Storage Explorer (preview) and right click the blob you want access to.
Select Get Shared Access Signature. You can edit the allowed permissions and the Start/Expiry dates.

Create a Transfer Site with SAS in Secure Transport
Create a Transfer Site under an existing User Account. Choose Azure Blob Storage from the Transfer Protocol dropdown menu.
Select Shared Access Signature for Connection Type, and paste the copied SAS in the SAS URI field. After a proper SAS is provided, the Storage Resource URI, SAS Parameters, SAS Signature, Azure Blob Container and Upload/Download Folder fields should be extracted from the SAS, if present, and auto-populated (the SAS Signature is sensitive data, so it is hidden).
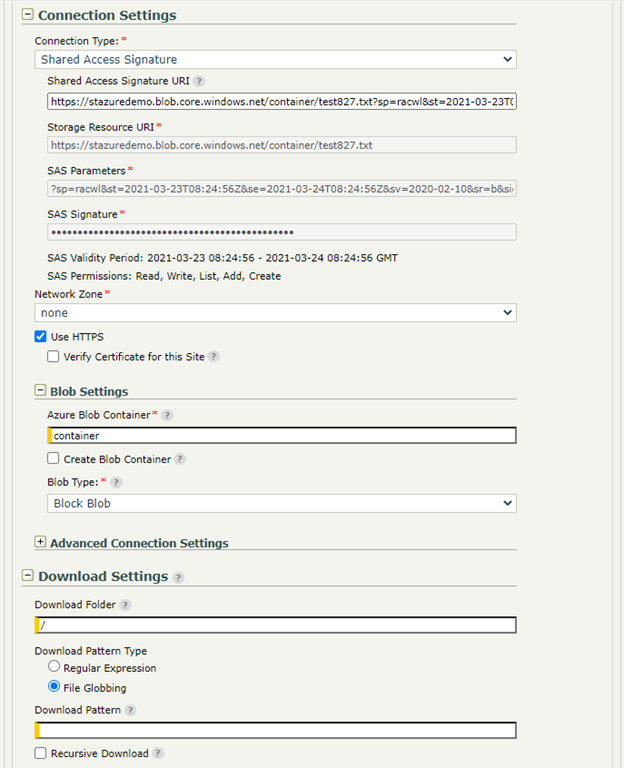
Download/Upload settings: Configure the download and upload settings as for a regular Transfer site, as well as any needed PTA settings.

Note: If present, Upload and Download Folder are extracted from the SAS. If the fields are empty, the root directory is used.
Test the Setup
Server Initiated Pull by ST
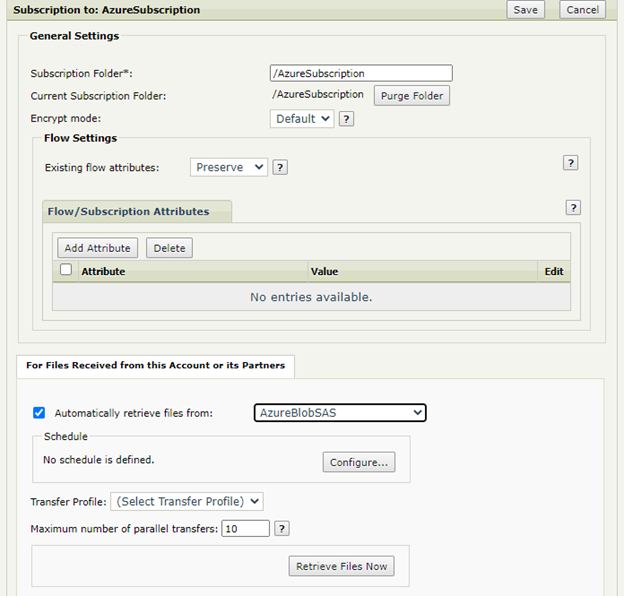
Create a Subscription to a Basic Application (BA).
In the For Files Received from this Account or its Partners section, select Automatically retrieve files from and select the Azure Blob Storage Transfer Site from the drop-down.
Set a schedule or alternatively, use the Retrieve Files Now button after the Subscription was saved (i.e. save the Subscription, re-open it and then use the button).
[optional] Under For Files Sent to this Account or its Partners, select Send Files Directly To and select a different Site where the test file should be sent to (local or remote location) after it's pulled from the Azure Storage.
Save the Subscription.
Place a test file in the Azure Storage account in the folder that was defined under "Download Settings" of the Azure Blob Storage Transfer Site in ST.
Wait for the scheduler to trigger or use the Retrieve Files Now button in the Subscription.
Go to Operations → File Tracking → Show Advanced Search, then filter by "Protocol: azure-blob" and make sure each of the transfers succeeded with green check Transfer Status icon.
Server Initiated Push from ST
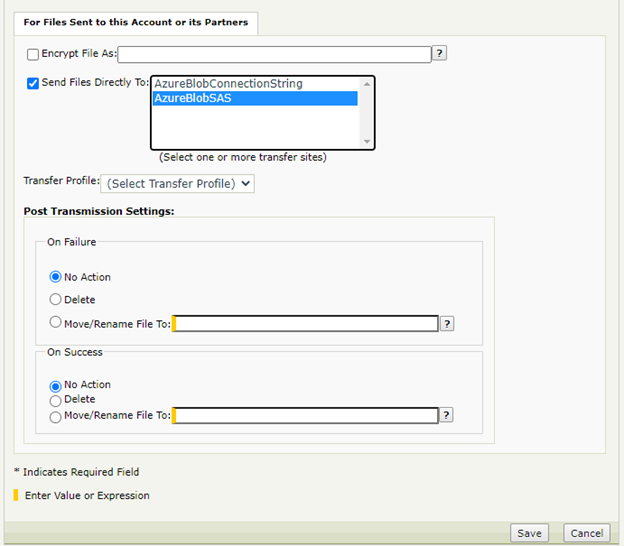
Create another Subscription to a Basic Application (BA).
Under For Files Sent to this Account or its Partners, select Send Files Directly To and select the Azure Blob Storage Transfer Site.
Login to ST with the user account and upload a test file in the Subscription Folder. Wait for a few seconds.
Go to Operations → File Tracking → Show Advanced Search, then filter by "Protocol: azure-blob" and make sure each of the transfers succeeded with green check Transfer Status icon.
If all have succeeded, go to the Azure Storage account and check the folder defined under "Upload Settings" of the Azure Blob Storage Site in ST. The file should be there.
Troubleshooting and Notes
To enable extended debug logging, edit the <FILEDRIVEHOME>/conf/tm-log4j.xml config file. Find the com.axway.st.plugins.site logger element and set its level value to DEBUG.
When a transfer to/from Azure has failed, the steps below can be used as guidelines how to troubleshoot the issue. Yet, as a first step, you should always verify that the Azure configuration and the Download/Upload parameters are correct and up to date.
- Go to Operations → File Tracking → Show Advanced Search, then filter by "Protocol: azure-blob".
- Click on the red X Transfer Status icon related to the failed transfer, expand the window and take a screenshot of the entire content. The screenshot will be requested by Axway Support in case it is needed to open a Support ticket.
- Click on the SessionID link, which redirects to the Server Log with filtered results related to the transfer session.
- Inspect the messages related to the transfer session.
- The detailed error/root cause is likely to be presented in these event messages. Click on the timestamp link next to the message that might hold the error. Expand the window. Detailed error message/stack trace is presented.
For a complete list, refer to the section Known Issues and Limitations in the README.md file included in the Azure Blob Storage Connector archive.