KB Article #176958
SSL Server Allows Cleartext Communication Vulnerability - QID 38143
Problem
Qualys software analysis tool may report QID 38143 as a potential SSL/TLS vulnerability. QID 38143 indicates that the server supports ciphers that include no encryption (i.e. Null Cipher Support) and this potentially can allow cleartext communication over HTTPS.
Resolution
To address the issue, you should disable all Null ciphers for TLS/SSL.
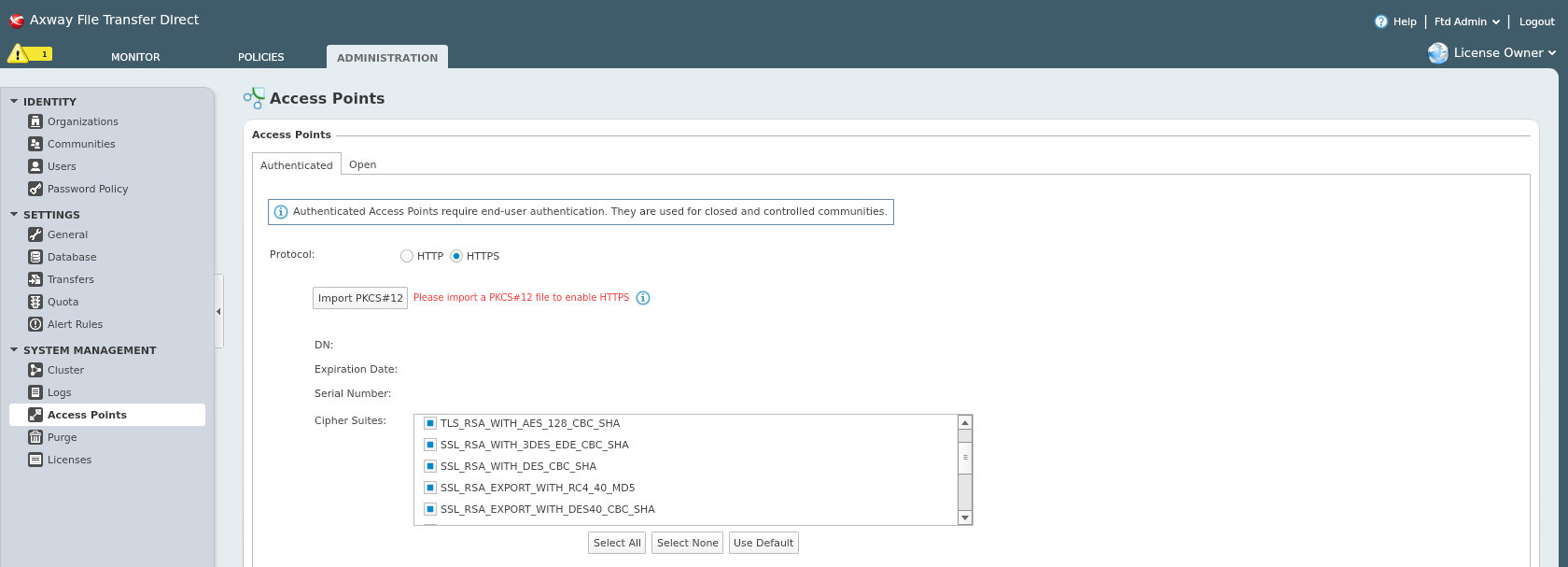
This can be done by the administrator under [License Owner] > Administration > Access Points (Authenticated/Open) > HTTPS
All ciphers that contain "WITH_NULL" in the cipher name should be disabled, namely:
SSL_RSA_WITH_NULL_MD5
SSL_RSA_WITH_NULL_SHA
TLS_ECDH_anon_WITH_NULL_SHA
Uncheck the relevant check-boxes and click Save. Please note that the application service will be restarted upon saving the settings.
Testing:
The test for QID 38143 can be verified manually with the openssl command line client. This client is commonly found on Unix based machines or can be found under CYGWIN on Windows as well.
On a command line, type:
openssl s_client -connect TARGET_IP:443 -cipher eNULL
Where TARGET_IP is the IP address of the host in question.
Expected output when QID 38143 is addressed:
CONNECTED(00000003)
21602:error:140790E5:SSL routines:SSL23_WRITE:ssl handshake failure:s23_lib.c:188:
For more information, you may also refer to the Qualys document about QID 38143