KB Article #178114
Unable to verify domain controller issued certificate with CRLDP protocol
Problem
Domain controller certificates issued by enterprise CAs use an Active Directory path as their CRL Distribution Point (CDP). The CDP URL format looks like "ldap:///CN=My CA,OU=...DC=example,DC=com?certificateRevocationList".
The problem with this default CDP format is there is no hostname in the URL to resolve the directory location and we don't have prior knowledge of the LDAP server's hostname. This will cause the Desktop Validator CRLDP validation protocol to fail.
Resolution
There are few possible resolutions. One is to use OCSP but if this isn't possible the issuing CAs certificate template for domain controllers could be modified to include the hostname in the CDP. The other option is publish the CRLs to a webserver and use an HTTP URL in the CDP. Please refer to vendor documentation for this. Here's a starting point for more information:
https://technet.microsoft.com/en-us/library/cc7308...
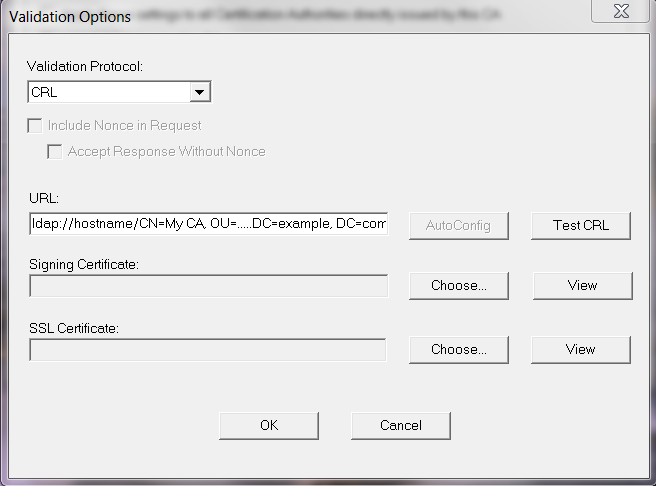
The other option is to configure Desktop Validator with a CA specific validation option for the CA containing the incomplete CDP. The configuration will be similar to the figure below with a valid URL containing the hostname. The URL and connectivity to the CRL can be verified using the TestCRL button.